To paraphrase Henry Kissinger, “It is not often that [companies] learn from the past, even rarer that they draw the correct conclusions from it.” At Link Labs, we hope to break this trend when it comes to security in the Internet of Things (IoT). Most people are aware of the cyber security issues consumers and businesses face when it comes to the internet, cloud computing, electronic payments, mobile, and the myriad of other technologies. The reason that security is such a major issue in cyber computing is that measures were often considered only after launching a product or new technology. In short, you can’t easily retrofit security.
With that in mind, take a look at the Google Trends chart below. This shows the popularity of search terms over time. As you can see in blue, “Internet of Things” has taken off as a search term… and it currently sits at its most popular point in Google history (as of January 2015). But check out the red line. That is how the search volume for “Internet of Things security” stacks up against “Internet of Things” in popularity over the same time period. I would not expect IoT security to approach IoT in terms of popularity, but I bet the relative magnitude might have had a different story to tell.
It’s a good visual of the prioritization going on in the IoT. Companies see a $19 trillion opportunity, and they want to rush into development and often times security becomes a casualty of time-to market. Sound familiar? This is exactly why we’re seeing major breaches at Home Depot and Target, and why the IoT is susceptible to hacks.
Plan For Your Internet Of Things Security Challenges
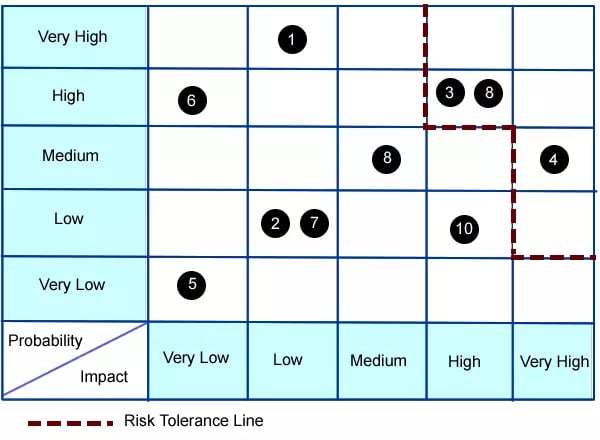
Although it seems like we’re already down this path of no return as an industry, there is still hope. And it starts with you, your company, and the IoT application you’re building. You need to consider the Internet of Things security challenges you face before completely building out the technology. Here’s one way how. The Risk Matrix For IoT Security A risk matrix is a basic method in risk management that compares the probability of risk to the impact of that risk. If a certain risk is highly probable and also highly impactful, that issue becomes priority one. You need to focus on stopping that threat first.
A risk tolerance line can be established by your team in order to help you prioritize your IoT/M2M security challenges. If impact is medium but the probability is very low, that item may fall below your risk tolerance line and you will not focus on it. Obviously with an unlimited budget or an outside firm who can ensure security, you’ll be able to safely secure all access points to your system. That is ideal. By the way, we’d like to reiterate the fact that “risk tolerance” is not a dependent variable of “time-to-market.” But, if you’re going it alone, we recommend starting with the risk matrix process you see above. Here are some typical security issues that may be facing an IoT application:
- AES public/private key exchange methods
- Protecting attached TPC/IP networks from intrusion through your device
- Protecting pre-shared keys from reverse engineering through an MCU debugger
In summary, we recommend outlining all of the M2M security challenges facing your application. Then, chart them out on a risk matrix and prioritize your concerns. How well can you safely secure the top priorities and all following concerns? Drop us a line if you’d like some help from a Link Labs engineer about your specific Internet of Things security challenges.